On a recent engagement I was tasked to conduct a penetration test against an Intune enrolled iPhone with an initial foothold of physical authenticated device access. During the test I discovered a security vulnerability, in the Microsoft Company Portal App, which allows an attacker to reset the device’s passcode without having to enter the current pin or reauthenticate to the App, thus, providing persistent access to the phone and AppleID. This vulnerability has been successfully exploited both during the commercial test and within my own controlled environment to confirm findings. This blog post will provide a step-by-step walkthrough of the finding.
Confirmed vulnerable version:
iOS devices running Company Portal Version =< 5.2311.1
Prerequisites
- Authenticated Access to an enrolled iPhone.
- Authenticated Access to the Company Portal Application.
Steps to Reproduce
Open the Company Portal Application.
On the “Apps” tab, select “Company Portal Website”
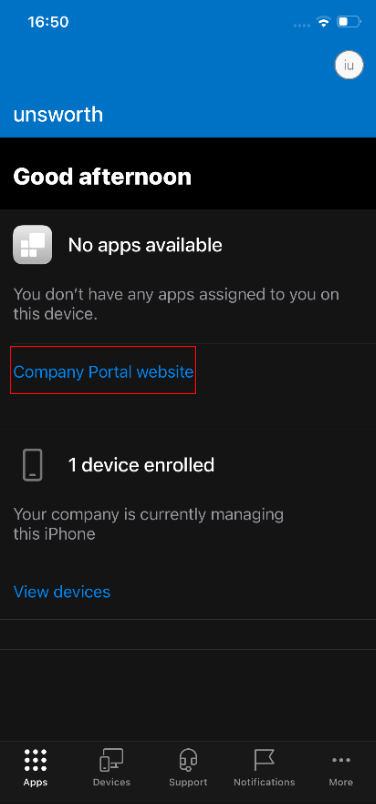
When the page opens, press “Devices”
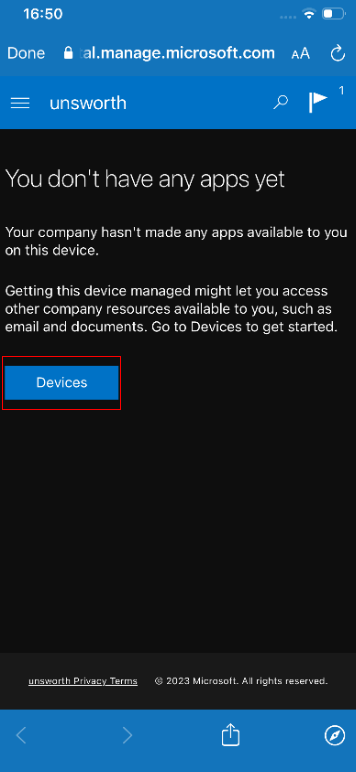
When the devices page opens select the device you are currently using:
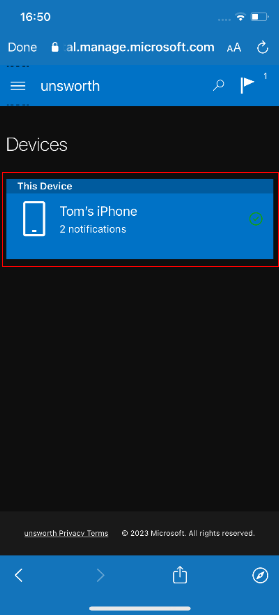
Press the three dots to expand the menu and press “Reset Passcode”:
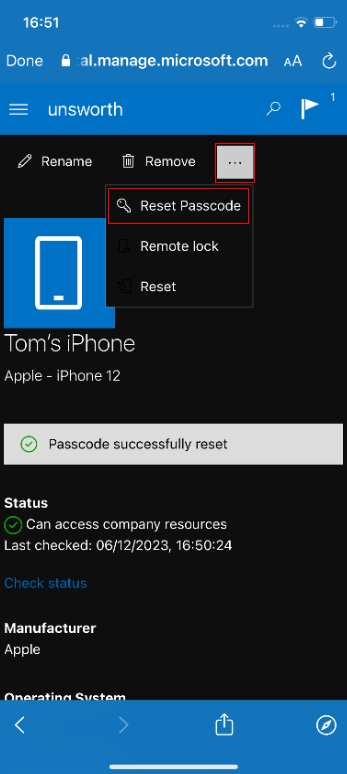
You are required to reauthenticate before the passcode can be reset, however, you can bypass this by pressing “Sign out”, waiting and then pressing the back button. You can also reauthenticate by pressing “done” in the top left and then opening the company portal website again by repeating the previous steps.
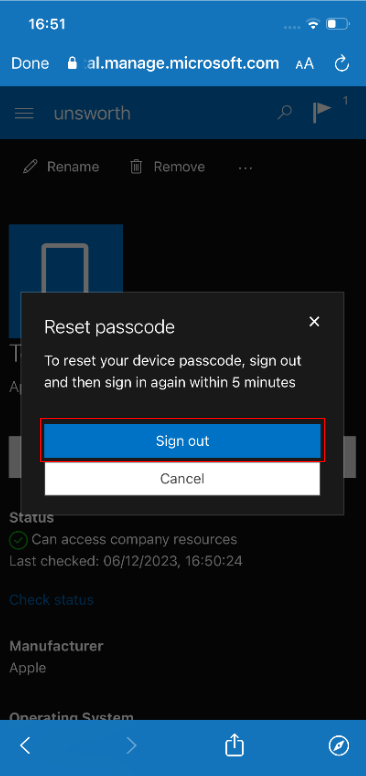
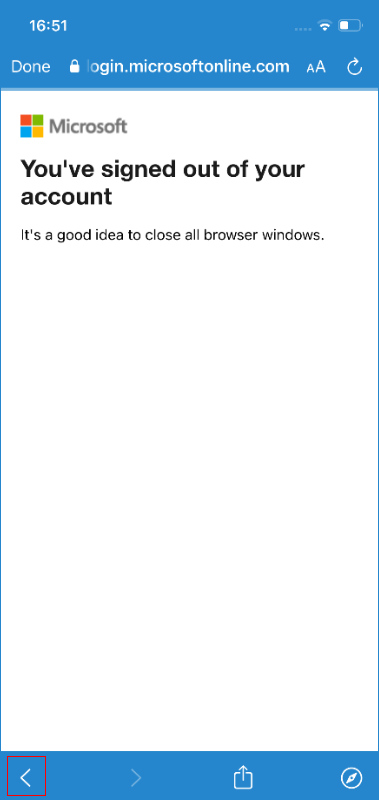
This procedure causes the application to behave as if you have successfully reauthenticated, allowing you to access the “Reset Passcode” functionality. Typically, this feature will remove the current passcode from the device. If an Intune policy exists that requires the device to have a passcode set, then the app will prompt the user to enter a new code after the current pin has been removed. This prompt may also be trivially bypassed by simply backgrounding the application by pressing the home button.
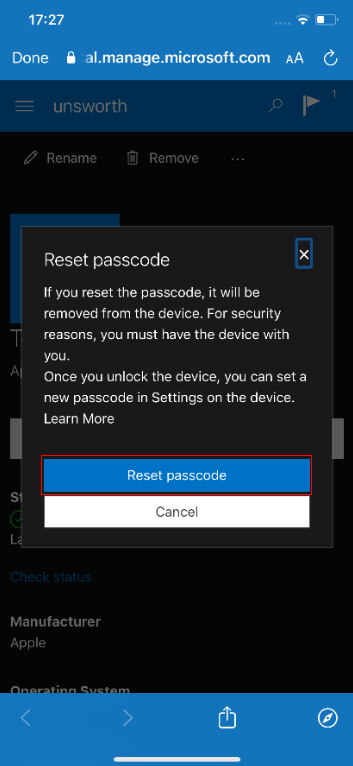
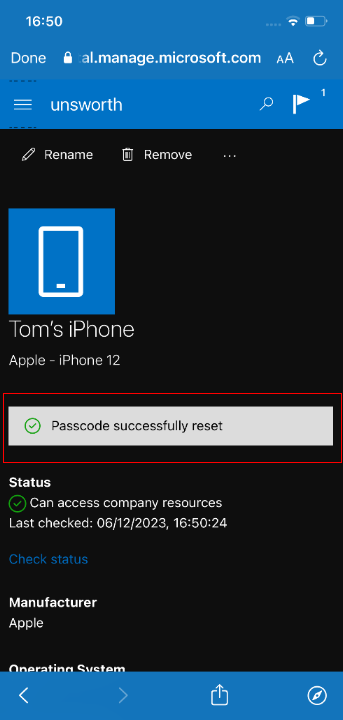
Check out the video below to see the vulnerability in action:
Conclusion
This is a simple attack that doesn’t require technical expertise to conduct and has serious consequences as the attacker has gained persistent access to the device. Additionally, if the phone number associated with the target device’s SIM card matches the number assigned to the AppleID account, then further attacks such as resetting the user’s Apple ID password and factory resetting the phone will also be possible.
The vulnerability was reported to Microsoft on the 7th of December 2023. Microsoft confirmed the vulnerability and passed on the relevant information to their app team on the 22nd of December 2023. As of the time of writing, the issue has been acknowledged and a patch is expected to be released.