Introduction
Since the early 1900’s, radio guided drones or Unmanned Aerial Vehicles (UAVs) have been an important part of military aerospace, the first UAV torpedo being used in 1917 named the “Kettering Bug” (Daly, 2020) and an affordable radio-controlled aircraft for target practise the “de Havilland DH82B Queen Bee” (Daly, 2020) representing two such technologies in use before the turn of the century.
Today, the use of UAVs has surpassed use in a singularly military function and is becoming an innovative and efficient option for commercial enterprises, helping to perform a plethora of business assignments and joining the ever-expanding cyberspace of the Internet of Things (IOT). Amazon’s use of drones for their delivery services is currently being perfected and the use of drones to perform topographical surveys greatly reduces the cost of utilising manned aircraft to obtain the same results.
The technical capacity and the increased material availability also give drones and UAVs a considerable advantage in terms of mass deployment on the modern battlefield. The use of unpiloted machines for targeting, reconnaissance and as a delivery mechanism for explosives has been well documented, but the War in Ukraine has displayed that smaller commercial drones can be outfitted with military hardware to provide similar capabilities at a fraction of the cost attributed to conventionally manufactured military drones.
This paper aims to explore the impact of exploiting vulnerabilities within commercially available drones, looking in depth at their communication protocols and the general attacks surfaces they present.
Through analysis and examination of the UAV communication protocols, software architectures and hardware components, this document will seek to uncover the weak points that adversaries may target to compromise drone operation.
Practical Analysis of Drone Communications
The drone used for practical testing of these protocols is a Chinese replica of a series of Mavic drones, branded “Emotion Drone”.

Figure 1: Emotion Drone (Eachine E58)
Figure 1 shows the internal circuitry of the drone with two identifiable chips present upon initial opening of the drone’s top cover. One being the XN297LBW a short-range wireless transceiver integrated circuit (IC) and the other a gyroscope MP67B chip.
Upon further research, the functionality appears to have close similarities to the Eachine E58 pocket drone.
The drone itself acts as a mobile router with built in DHCP, allowing the controller to connect as a client to the Wireless Local Area Network (WLAN) with the 802.11 standard acting as the medium through which commands are sent to the drone. This WiFi network is unprotected and, with any actor being able to connect to the network, falls under the Common Weakness Enumeration “CWE-284: Improper Access Control” (MITRE, 2023)
The openness of the WiFi network is particularly interesting as many reproduction drones make use of open access points within their communications architecture leaving them open to similar attack surfaces.
Per contra, the original DJI drone designs appear to require the operator to connect their phone to a separate physical remote control before a communications channel between the phone and the drone can be established.
The instruction manual, contained with the “Emotion” drone, details using an application available on both Apple and Android app stores named FYD-UAV which, when installed, streams a video feed from the drone’s camera to the phone and presents a graphical user interface from which the pilot can control the flight of the drone in First Person View (FPV).
By identifying the WiFi communication link, an abundance of other vectors for obtaining information about the drone can be explored. During a test flight of the drone, it was possible to sniff the network traffic using Wireshark by placing a wireless adapter into monitor mode and capturing packets that were transmitted between the controller (in this case an iPhone) and the drone.
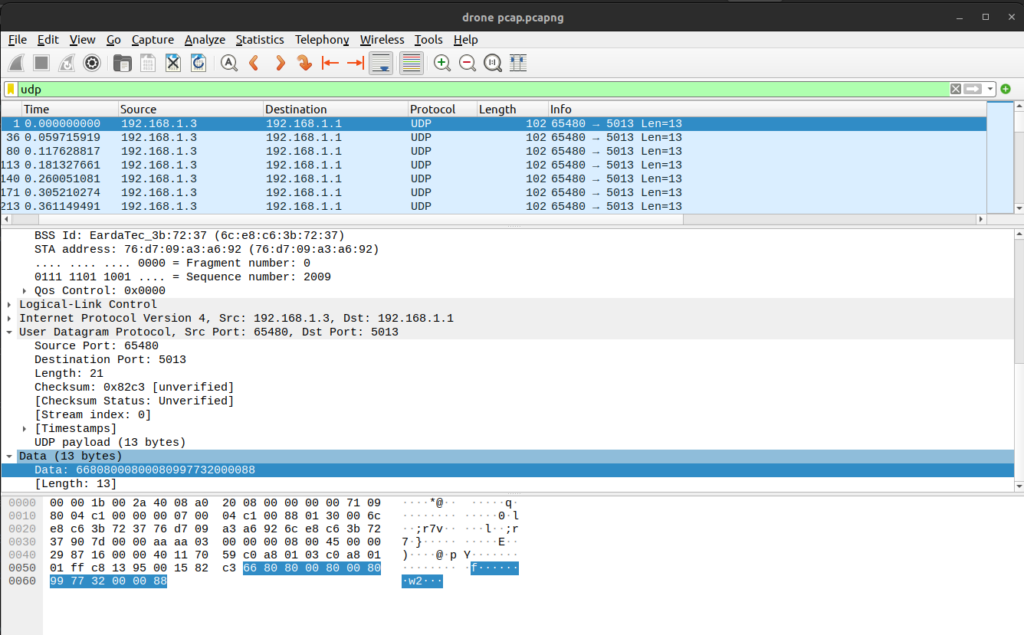
Figure 2: Packet Capture of UDP communication from Controller to Drone
Figure 2 shows an excerpt of the captured data being sent to the drone, with the source IP address 192.168.1.3 representing the controller and 192.168.1.1 address representing the drone.
The highlighted “Data” field in Figure 2 defines the instructions sent to the drone which the drone decodes as actions to perform including stabilisation and flight control. Further analysis of the packets shows that each of these instruction frames is encompassed within header and footer hexadecimal characters, namely “66” as the header and “88” as the footer. This confirms that the drone is vulnerable to “CWE-319: Cleartext Transmission of Sensitive Information” (MITRE, 2023)
Analysis of Information Controls
Looking at the drone as an individual entity provides one method of determining the data that can be extrapolated, but analysis of the controller also gives deep insight into the information controls applicable to the drone.
The application intended as the companion to the drone, obtained through the Android store describes two functions that reveal interesting vectors for compromise of the drone:
“1. Displays a live feed taken by the on board camera.
2. Record and store photos and videos on smartphone.” (FYD Technology Co. Ltd, 2023)
To further discern the inner working of this functionality, the application’s Android Package (APK) was extracted from the phone and transferred to a Ubuntu host for further examination.
The APK was first converted into a Java Archive (JAR) file using the Dex2Jar program. Once in the JAR format, analysis was performed through the Java Decompiler Graphical User Interface (JD-GUI)
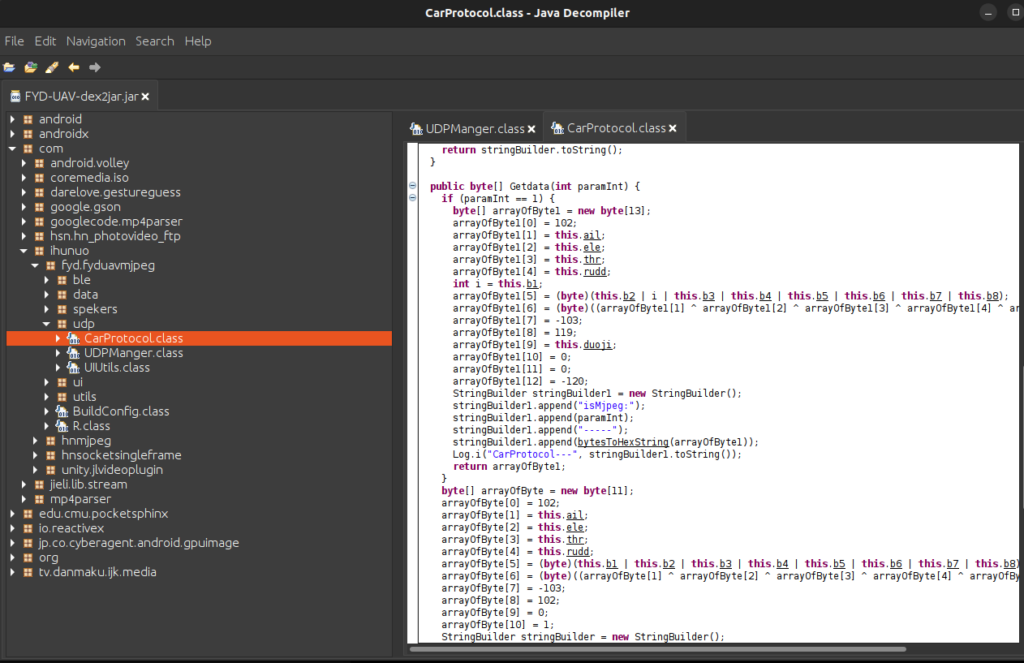
Figure 3: CarProtocol Byte Arrays
Figure 3 above displays the Java Class for structuring byte arrays as instructions which the drone receives as directions to the motor for controlled flight.
Some variables of interest were noted such as “ail”, “ele”, “rudd” and thr” which are likely references to the flight control surfaces as below:
ail – Aileron – Used to control the longitudinal roll of the drone
ele – Elevon – Used to control the forward and backwards pitch of the drone
thr – Thrust – Used to control the acceleration of the motors and height of the drone
rudd – Rudder – Used to control the direction of the drone (simply the left and right facing of the drone)
This code works in conjunction with another Java Class “UDPManager” and these arrays are used to define the hexadecimal instructions sent via User Datagram Protocol (UDP) to the drone via port 5013.
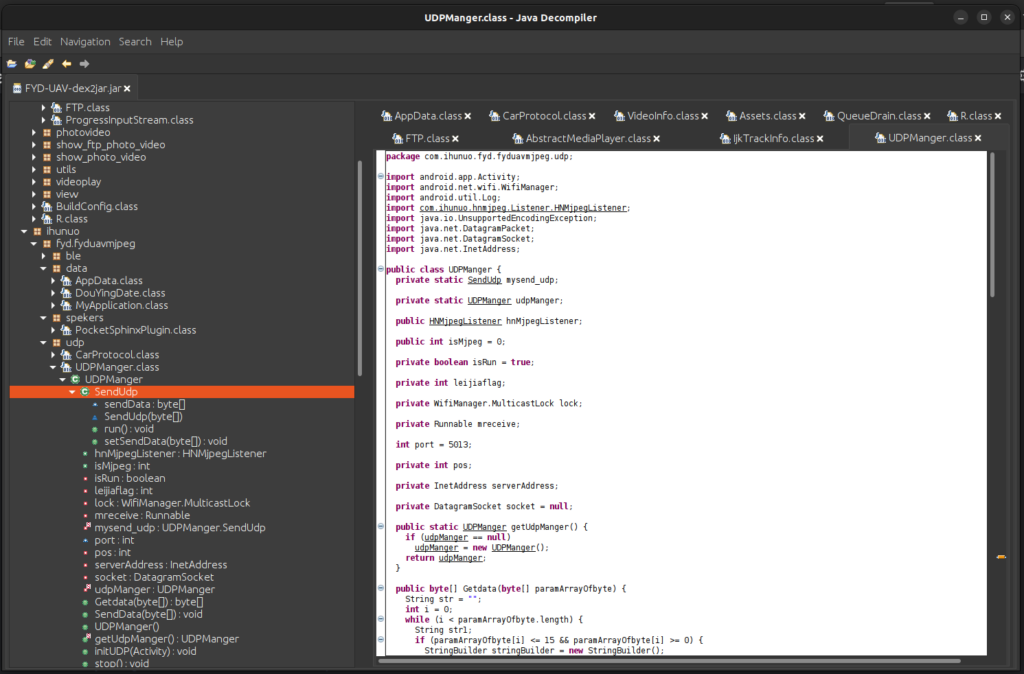
Figure 4: UDPManager Java Class
Figure 4 shows the “UDPManager” java class containing the method by which the byte protocol is implemented and sent across the network to the drone. The code includes the specific port that is used by the drone to receive the data.
By cross referencing the patterns in the UDP transmissions previously identified in the initial Wireshark logs, it is possible to identify the position of the hexadecimal commands in the UDP payload data and observe the exact commands sent to the drone by sniffing the wireless traffic.
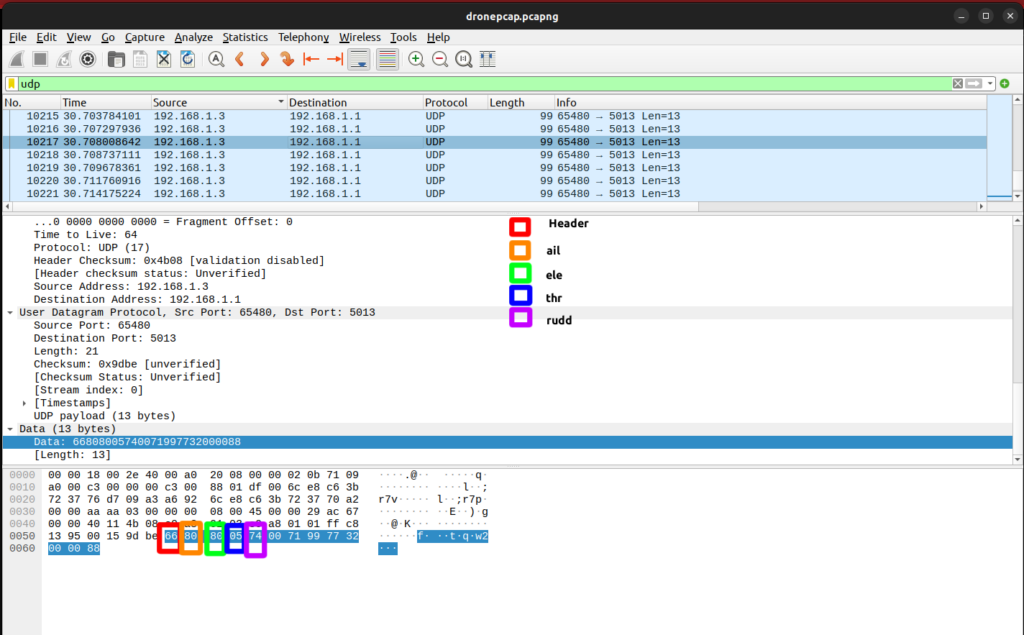
Figure 5: Cross reference of the Wireshark capture
Above, figure 5 identifies the four major components of the drone’s control surface within the captured packets sniffed from the wire.
The analysis of the controller software reveals deep levels of information about the drone’s flight functionality and the security implications extend beyond the security of the application alone. An adversary with this information could craft packets and, using a wireless adapter, could deliver payloads of alternative instructions to the drone causing Denial of Service conditions or simply instructing the drone to fly at the behest of the attacker.
Further investigation of the APK provides another intriguing piece of code which lies within the “hsn.hn_photvideo_ftp” and is named simply “FTP”. This snippet of code reveals the login details to access to File Transfer Protocol (FTP) server of the drone where video and images of from the drone’s camera are stored.
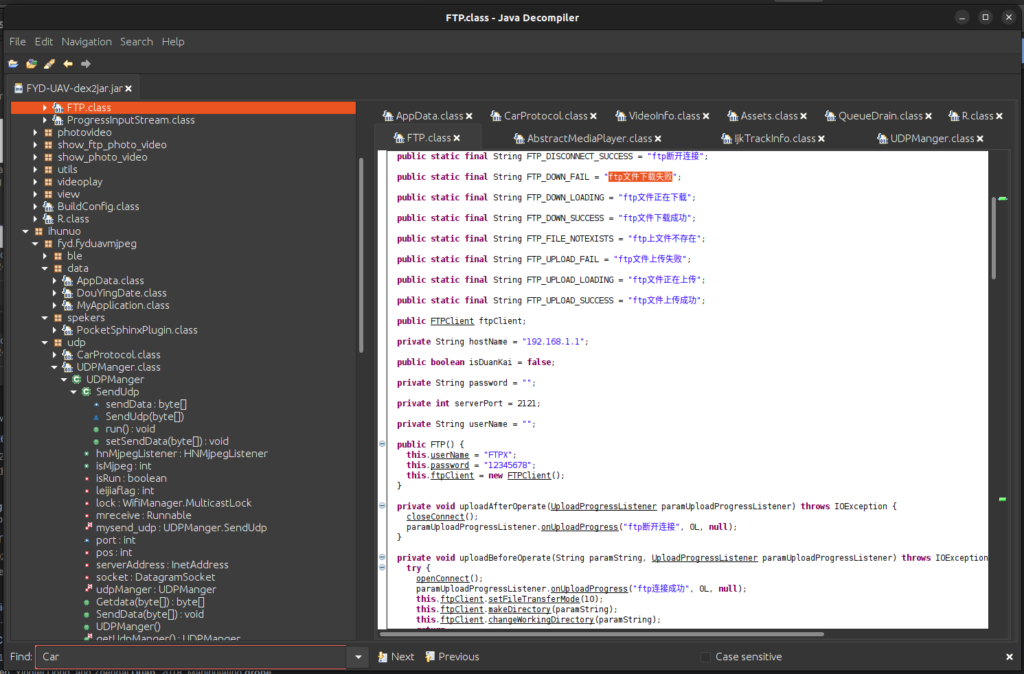
Figure 6: FTP Controller Code
With the credentials for the drone’s FTP server stored inside the controller application’s data, the entire system is vulnerable to both “CWE-312: Cleartext Storage of Sensitive Information” and “CWE-256: Plaintext Storage of a Password” (MITRE, 2023)
Due to the time constraints of the project being undertaken, a complete reverse engineering of the bespoke FTP client was not possible, but the findings make this conceptually possible and with further time could exacerbate the vulnerabilities already discussed.
The openness of the data-channels seen in the previous examples act as a simplified analogy for the wider attack surface presented by UAVs.
Real World Analysis of Drone Vulnerabilities
particularly volatile case-study for the identification and prevalence of drone vulnerabilities can be seen in the current conflict between Russia and Ukraine where “reliance on cheap but powerful first-person-view drones in recent months has made their pilots prime targets beyond the frontlines” (Snodgrass, 2023)
Russian Electronic Warfare (EW) equipment is being deployed in quantity to counter the Ukrainian personnel piloting the re-modelled, commercial and military drones with “an approximate distribution of at least one major system covering each 10 km of front” (Watling & Reynolds, 2023)
As discussed in the dissection and analysis of the “Emotion” drone, once a communication channel has been discovered, one of the most effective ways to attack a UAV is to disrupt the data flowing between the controller and the airborne system.
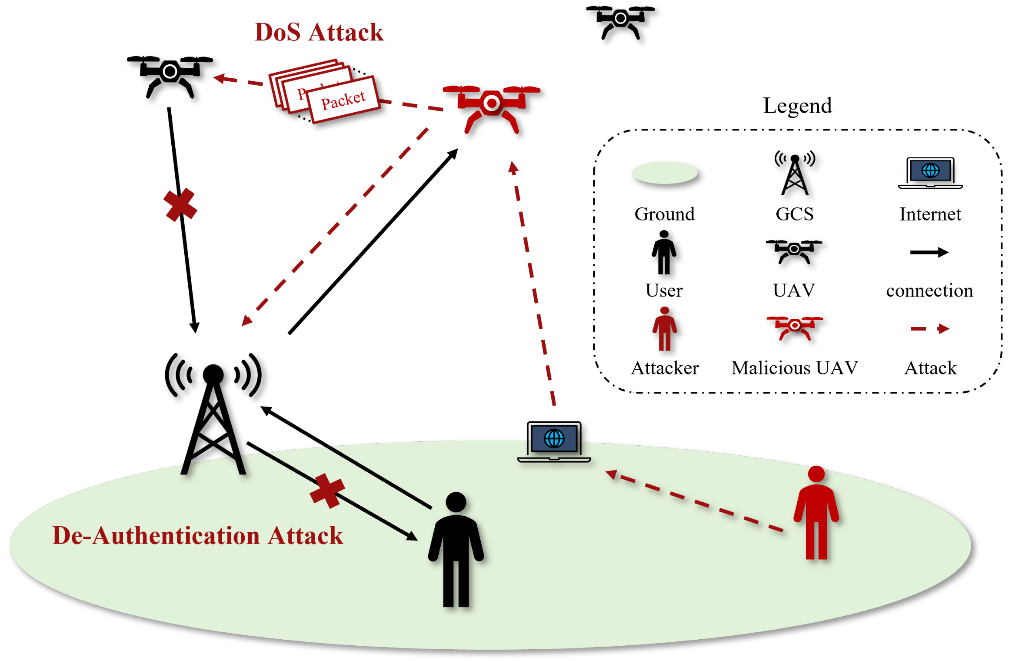
Figure 7: De-Authentication Denial of Service
Figure 7 details an overview of a Denial-of-Service condition in which the attacker’s drone in red is inundating the drone it is targeting with more data packets than it can process causing dissociation with its controller.
The conditions of this Denial-of-Service can be replicated on the “Eachine” drone by performing a simple WiFi de-authentication attack between the drone and its controller, essentially severing the communication channel.
The principles of this attack are mirrored in Russian EW equipment such as the Krasukha platforms and the Repellent-1, used to disrupt drone flight patterns and act as Communications Jamming (COMJAM) systems to supress the signals between the drones and the controller.
For more advanced drones that make use of Global Positioning System (GPS) and alternative communication frequencies, the concept behind attacks on UAVs remains the same and systems like the RP-377 (Lorandit) perform radio jamming by broadcasting “signal-blocking noise over a wide band of different frequencies” (Axe, 2023).
Ukrainian ground personnel are also using drone jamming equipment effectively and an impressive tactical backpack created by Kvertus Technology which is capable of “blocking the 2.4 GHz, 5.8 GHz, and 1.6 GHz frequency ranges commonly used for remote guidance, navigation, and control of various commercially available UAVs” (armyrecognition.com, 2023)
A further vector that affects commercial drones specifically can be seen in DJI drones which feature a signal named “AeroScope” initially implemented “in response to growing government concerns about drone flights near airports and critical infrastructure” (De Jager, 2022)
This signal is an unencrypted stream of information containing a drone ID and, dangerously for the operator, the operator’s physical location.
Similarly, to how the “Eachine” drone transmits instructions about the flight patterns in a way that can be intercepted and read by an adversary, the DJI drone’s broadcasting of the drone and pilot’s position using longitudinal and latitudinal co-ordinates constitutes a catastrophic loss of Operational Security (OPSEC).
This vulnerability has been designated its own Common Vulnerability and Exposure ID (CVE) “CVE-2022-29945” due to the broadcasting of “unencrypted information about the drone operator’s physical location via the AeroScope protocol.” (MITRE, 2022)
With DJI drones being used in a military capacity in the war in Ukraine, the results of the security implications have been severe and well documented with drone operators now finding themselves targets as a result of the security vulnerabilities present within the drone’s wider communication systems.
Remediating Commercial Drone Vulnerabilities
Drone manufacturers looking to secure their products and restrict the attack vectors present on their designs can implement some controls by understanding the common weaknesses and addressing them individually.
Using the examples discussed in this paper, it is possible to highlight some brief high level remediations which could be applied to reduce the avenues for exploitation on the drones.
- CWE-284: Improper Access Control
A manufacturer could implement access controls that disallow certain types of traffic or devices from accessing interfaces on the drone’s communication array.
In the example provided in the practical analysis, an access control list built into the drone’s access point, which allows only one client to communicate on the network, would stop adversaries from logging into the network and performing further attacks and enumeration on the drone and its communication channels.
- CWE-319: Cleartext Transmission of Sensitive Information
Implementation of Transport Layer Security (TLS) to encrypt communications between the drone and its controller would ensure that attackers sniffing the network traffic would not be able to understand its context as easily and would make attempts to reverse engineer the protocols that the drone uses significantly harder.
- CWE-312: Cleartext Storage of Sensitive Information & CWE-256: Plaintext Storage of a Password
The remediation of the cleartext storage of information and credentials on the controller software is an issue that would need to be addressed in conjunction with the drone’s on-board architecture. Manufacturers could investigate implementing cryptographic algorithms and key based encryption to store the passwords at rest in a secure manner.
Furthermore, by performing hashing functions on credentials and sensitive data with appropriate strength and complexity, a drone manufacturer can ensure the confidentiality of the sensitive information, which does not need to be viewed by the operator and can be stored effectively on the drone’s communication systems.
Conclusion
As drones and the Internet of Things become more prevalent in human evolution, it is important to understand the wider implications of secure communication transmissions between unmanned systems.
In both commercial and military capacities, the changing use of drones and the security architecture of UAV systems marks a tangible collide between cybersecurity and the physical world. It highlights the importance of ensuring that unmanned aerial systems maintain a well defended communications platform to resist unauthorised actors from performing actions that would compromise the intended function of the drone.
References
Daly, David (10/06/2020) “A Not-So-Short History of Unmanned Aerial Vehicles (UAV) “
Available at: https://www.iwm.org.uk/history/a-brief-history-of-drones
MITRE (26/10/2023) “CWE-284: Improper Access Control”
Available at: https://cwe.mitre.org/data/definitions/284.html
MITRE (26/10/2023) “CWE-319: Cleartext Transmission of Sensitive Information”
Available at: https://cwe.mitre.org/data/definitions/319.html
FYD Technology Co. Ltd (23/08/2023) “FYD-UAV”
Available at: https://play.google.com/store/apps/details?id=com.ihunuo.fyd.fyduavmjpeg&hl=en&gl=US
MITRE (26/10/2023) “CWE-312: Cleartext Storage of Sensitive Information”
Available at: https://cwe.mitre.org/data/definitions/312.html
MITRE (26/10/2023) “CWE-256: Plaintext Storage of a Password”
Available at: https://cwe.mitre.org/data/definitions/256.html
Snodgrass, Erin (31/12/2023) “Russians are hunting the Ukrainian drone pilots destroying their tanks and firing everything they’ve got, if they pick up their electronic trail, operator says”
Available at: https://www.businessinsider.com/russians-hunting-ukrainian-drone-pilots-destroying-tanks-electronic-warfare-2023-10?r=US&IR=T
Watling, Jack & Reynolds, Nick (19/05/2023) “Meatgrinder: Russian Tactics in the Second Yearof Its Invasion of Ukraine”
Available at: https://static.rusi.org/403-SR-Russian-Tactics-web-final.pdf
Axe, David (22/12/2023) “More And More Russian Vehicles Have Drone-Jammers. Ukrainian Drones Blow Them Up Anyway.”
Available at: https://www.forbes.com/sites/davidaxe/2023/12/22/more-and-more-russian-vehicles-have-drone-jammers-ukrainian-drones-blow-them-up-anyway/
Armyrecognition.com (07/12/2023) “EDEX 2023: Ukrainian company Kvertus presents counter-drone systems”
Available at: https://armyrecognition.com/defense_news_december_2023_global_security_army_industry/edex_2023_ukrainian_company_kvertus_presents_counter-drone_systems.html
De Jager, Wiebe (09/05/2022) “DJI drones transmit location data unencrypted; ‘open source AeroScope’ in the making”
Available at: https://dronexl.co/2022/05/09/dji-aeroscope/
MITRE (29/04/2022) “CVE-2022-29945“
Available at: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-29945
Appendix
Figure 7. “De-Authentication Denial of Service”
Bin Son, Seok & Hwa Kim, Dong (25/02/2023) “Searching for Scalable Networks in Unmanned Aerial Vehicle Infrastructure Using Spatio-Attack Course-of-Action“
Available at: https://www.mdpi.com/drones/drones-07-00249/article_deploy/html/images/drones-07-00249-g001.png