Introduction:
As of September 2023, there are 33.6 million cars on the road in the UK [1], and an estimated 1.48 billion vehicles on the road globally [2]. Given their importance to life as we know it, you may assume cars are well secured; but this is not always the case. This whitepaper will focus on the key fobs used to gain access to the vehicles and rolling code security, while also testing a few vehicles against known vulnerabilities. At the end, a potential remediation is recommended.
Flipper Zeros and Car Hacking:
To demonstrate the vulnerabilities in this paper we have used a Flipper Zero, however we felt it important to discuss a few points, especially with talks of banning the Flipper Zero in Canada. While the videos below show its use to gain physical access to cars, these exploits are NOT practically possible using a Flipper Zero and it cannot be used to go out and steal cars in the ways shown in this paper. This is partly due to the requirement of jamming in the attack chain, which we have omitted from this test as it is illegal. The Flipper Zero uses a Texas Instruments CC1101 [8] transceiver with a maximum transmit power of 12 dBm [9] (roughly 15mW). At this power level, effectively jamming a signal is not on the table. It’s not even in the dining room. The Flipper Zero also cannot transmit and receive simultaneously, so any capture while jamming would be impossible with a singular device.
Tools such as the Flipper Zero do not introduce any new vulnerabilities, they just make it easier to exploit existing vulnerabilities. Banning tools such as the Flipper Zero does nothing to address the underlying vulnerabilities in products, whereas implementing regulations on automotive manufacturers mandating higher security directly addresses the issue.
Rolling Code:
Rolling code is a system that generates a new code for each transmission, which is vital to the security of key fobs. To achieve this, both a transmitter and receiver keep track of a counter variable which is set when the transmitter and receiver are paired. This counter is incorporated into the key generation process and ensures that a different key is created every time. The counter value will then be added to a base value to create the final cryptographic key. In an automotive system, this base value is generated and agreed between the key and receiver when the key fob is first paired to the car. On the receiver side, the counter value is compared to the previous counter value and if it is within a certain range, for example c+1 -> c+5, then the receiver will accept the transmission. This is important to have, as sometimes the key may be pressed accidentally while beyond the receiver’s range, Without this contingency implemented, it would mean that when the key once again became within range of the vehicle and the user attempted to unlock it, they would be unable to do so. This is because the counter value would be different. To make sure the counter keeps up to date, every successful unlock transmission will also update the counter, so that the window is increased from
the new base counter value. Using this system, each transmission is only valid for a single use, and if an attacker was to intercept a transmission and attempt to replay it later, they will not be successful as the counter value will be lower than what the receiver will now accept.
Attacks:
Replay Attack:
A replay attack is as simple as it gets. It requires only one radio and does not involve any jamming. To carry out this attack, the attacker needs to intercept a key fob transmission and replay it at a later date. All modern vehicles use rolling code to secure their key fobs against this attack, so it’s expected that vehicles are not vulnerable to this.
RollBack (CVE-2022-37418 [5], CVE-2022-37305 [6], CVE-2022-36945 [7]):
The RollBack attack is a time agnostic attack affecting a wide range of vehicles, hence why it has multiple CVEs. It requires two radios and involves signal jamming. First, the attacker will jam the signal and capture the first unlock code. They will then stop the jamming, but still capture the second unlock code. This will allow the owner to unlock the vehicle. To unlock the vehicle, the attacker will replay both captured codes in succession. In vulnerable vehicles, this can result in a resynchronisation of the counter to an earlier value, therefore allowing an old and previously invalid rolling code to be used again. The number of consecutive transmissions required to trigger the resynchronisation can vary from 2 to 5, and the time gap between the transmissions is also important. As this is a time agnostic attack, the user of the vehicle can lock and unlock the vehicle an unlimited number of times between the capture of the transmission and the replay [3]. The diagram below illustrates the attack process:
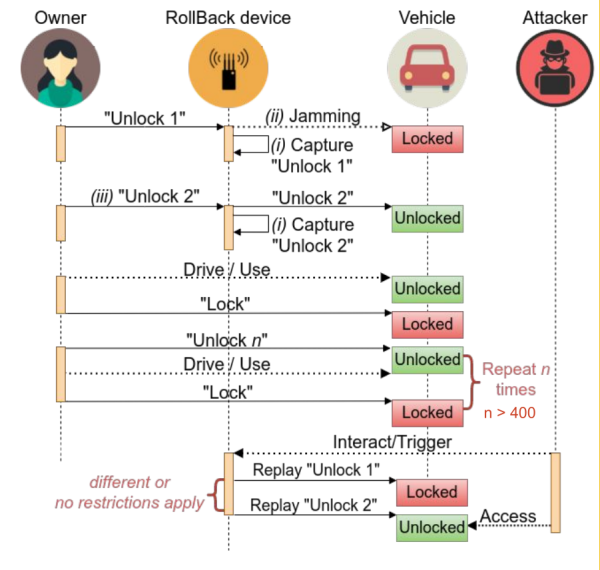
Figure 1: RollBack Attack Process [4]
Note: Signal jamming is illegal, so for the exploitation the jamming will be simulated.
Relay Attack:
You may have seen reports in the media (https://www.dailymail.co.uk/news/article-12790145/350-000-Rolls-Royce-GONE-30-seconds-Moment-key-car-thieves-steal-luxury-SUV-owners-driveway.html) or even videos on TikTok/Instagram (https://www.tiktok.com/@cctvbirmingham/video/7295624511829937441) that show people stealing high-end cars in seconds. The method commonly used for this is a relay attack. Modern cars using Passive Keyless Entry systems (PKE) only rely on the car detecting that the key fob is near to unlock the vehicle. These systems use the same technology to verify that the key fob is inside the vehicle which will allow the engine to be started.
This attack requires an antenna to pick up the signal from the key fob inside a house. A repeater must then be held nearby to the car to repeat this signal strongly enough for the vehicle to receive it. This usually involves two people, one with the receiver and one with the transmitter.
Unfortunately, we will not be able to test this attack as we currently do not have access to a test vehicle with this technology.
Exploitation:
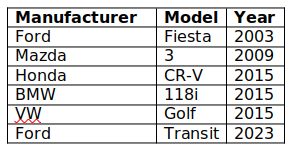
A variety of vehicles will be used as targets, with ages ranging from 2003 to 2015. The vehicles used are displayed in the table below:
Vehicle 1: 2003 Ford Fiesta
This car was expected to be vulnerable due to its age, however, it did present some issues not shown by the other vehicles. The first attack attempted was a standard replay attack, but upon receiving the old rolling code, the real key was desynchronised from the car, and it did not unlock. This is a risk when messing with your key fob and why it is not advisable to do this beyond a controlled environment. Fortunately, this vehicle has a method to resynchronise the key without any external software or assistance, but this is not the case for many vehicles.
Once the key was resynchronised, this vehicle was found vulnerable to the RollBack attack using 3 consecutive captured unlocks. When successful, this attack did not desynchronise the key. A video of this can be seen below:
Vehicle 2: 2009 Mazda 3
This vehicle gave some interesting results. While it was not vulnerable to the RollBack attack, the replay attack attempt had a different outcome. A simple replay attack did not work as this vehicle uses rolling code, however, when the same captured signal was replayed to the car 3 times, it triggered an unlock. This was surprising as it was the same, expired rolling code being replayed which should be disregarded rather than causing an apparent resynchronisation. This issue is similar to the RollBack attack assigned to Mazda (CVE-2022-36945); however, it differs in one important way. In this attack, only one key fob capture takes place, and this same capture is replayed to the vehicle 3 times. In the RollBack attack there are three consecutive captures which are then replayed back to the car. The result of this is that this attack is less complex and easier to carry out. A video of this exploit in action is available below:
Vehicle 3: 2015 Honda CR-V
This car was not vulnerable to a simple replay attack as expected, but it was vulnerable to a RollBack attack. The number of consecutive unlocks required to cause the resynchronisation for this vehicle was 5. It is not sensitive to the command used (lock/unlock) as long as the final command in the sequence is unlock. A video of the RollBack attack on this vehicle can be seen below:
Vehicle 4: 2015 BMW 118i
This vehicle was not found to be vulnerable to any of the attacks attempted. Interestingly, when analysing the captured key fob transmission, it appears to have a far higher complexity than the other vehicles tested so far.
2003 Ford Fiesta:
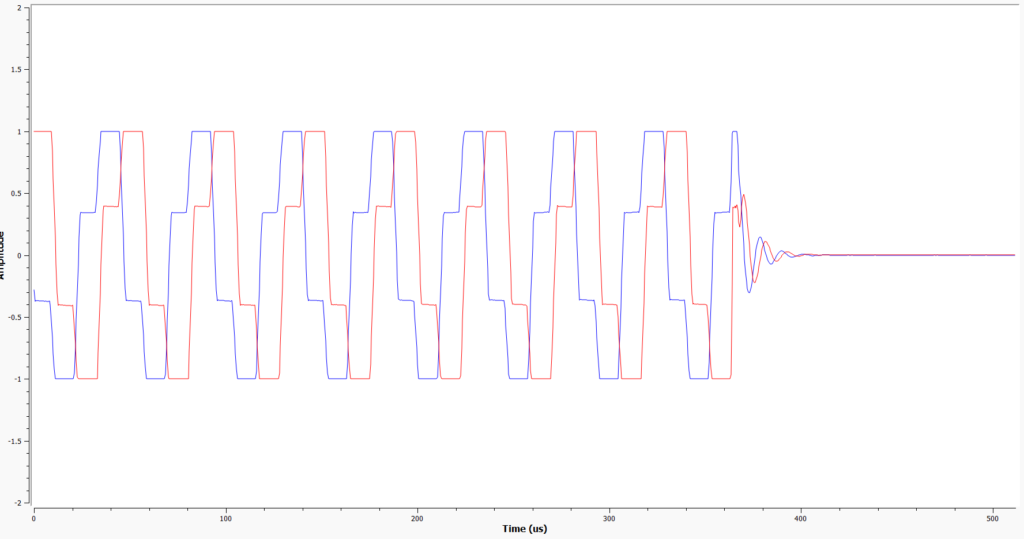
2015 BMW 118i:
In the image above showing the waveform over 500 microseconds, the BMW key is visibly transmitting more data than the key of the 2003 Ford Fiesta.
Vehicle 5: 2015 Volkswagen Golf
Tests on this vehicle also produced surprising results. When an old transmission was replayed to it, the vehicle completely shut off all communication with the key and required manual use of the key to access the car. This action forms part of the suggested remediation in the conclusion of this paper as it completely shuts down the possibility of an attack. The key also features a higher complexity transmission when compared to older vehicles.
Vehicle 6: 2023 Ford Transit
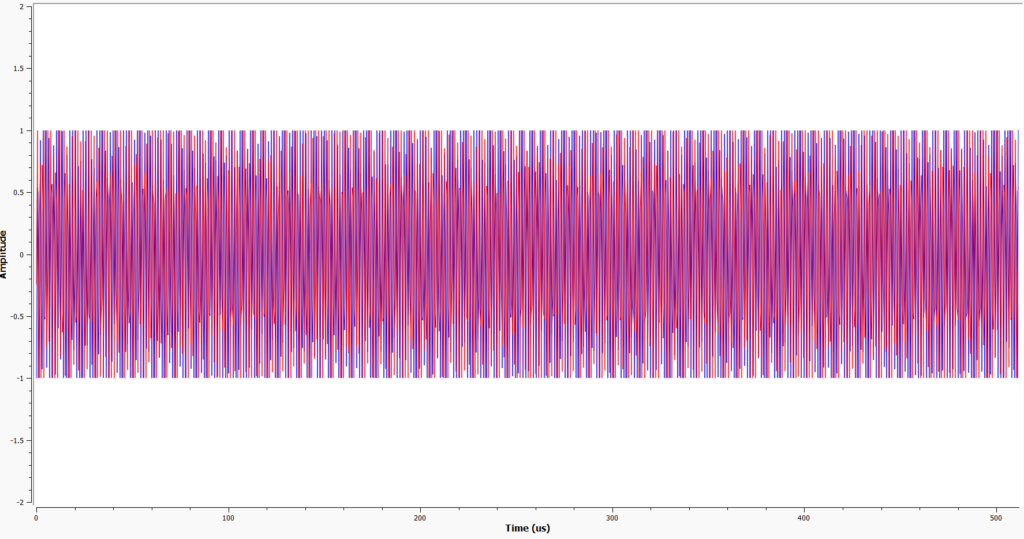
As expected, this vehicle was not vulnerable to any of the attempted attacks. This vehicle was produced in 2023 and should be implementing the latest security measures, which has adequately protected it against the comparatively old vulnerabilities used here. As with the BMW and VW Golf, the transmission from the key is far more complex when compared to the 2003 Ford Fiesta, showing the sheer difference in technology over 20 years. The waveforms below compare the two keys over a timeframe of 500 microseconds, the difference is visible:
2003 Ford Fiesta:
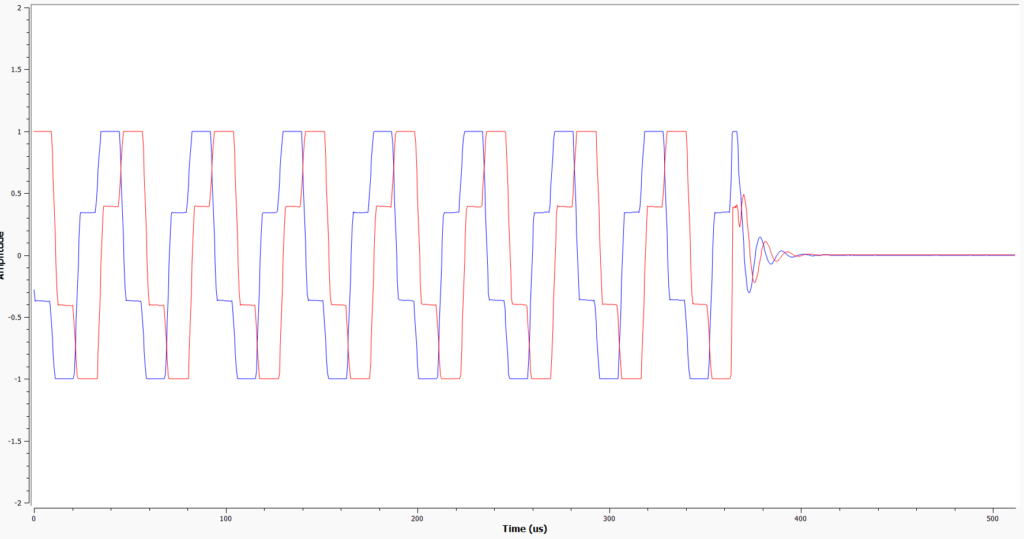
2023 Ford Transit:
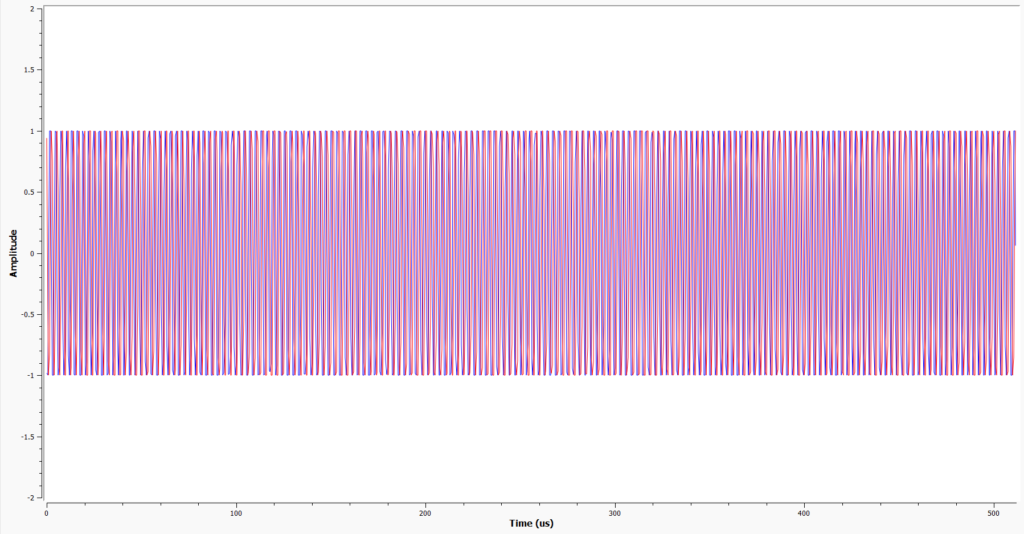
Remediation:
A suggested remediation to counter all attacks discussed is to implement a timestamp into each key fob transmission. When the vehicles receive the transmission from a key fob, even if the rolling code contained is valid, the unlock would not be carried out if the receival time was more than X seconds after it was created. The value of X could be changed depending on the manufacturer but, for optimal security, it should be no more than 5 seconds.
To increase the strength of this remediation, the vehicle could disable its ability to receive transmissions when it detects a potential attack, e.g. a transmission with an old rolling code is detected. This would completely shut down any potential attack, however it has the side effect of requiring the user to use the physical key to unlock the vehicle as shown with the 2015 Golf. Once the engine has been started, the receive functions could be re-enabled.
Sources:
[1] – https://www.racfoundation.org/motoring-faqs/mobility
[2] – https://hedgescompany.com/blog/2021/06/how-many-cars-are-there-in-the-world/ [3] – https://arxiv.org/abs/2210.11923
[4] – https://hackaday.com/2022/08/17/rollback-breaks-into-your-car/
[5] – https://nvd.nist.gov/vuln/detail/CVE-2022-37418
[6] – https://nvd.nist.gov/vuln/detail/CVE-2022-37305
[7] – https://nvd.nist.gov/vuln/detail/CVE-2022-36945
[8] – https://flipperzero.one/
[9] – https://www.ti.com/product/CC1101